An IP (Internet Protocol) address is a unique string of numbers separated by periods, assigned to each device connected to a computer network that uses the Internet Protocol for communication. It serves two main purposes: identifying the host or network interface and providing the location of the host in the network. Essentially, it’s like a mailing address for your computer on the internet. From a security and fraud prevention perspective, IP addresses serve as a crucial first step in identifying risk.
What is an IP Blacklist?
An IP blacklist is a database that contains a list of IP addresses that are known to be sources of spam, malicious activities, or other harmful behaviors. These blacklists are used by network administrators and email servers to filter out and block communications from these suspect IPs. By referencing these lists, organizations can prevent harmful interactions with known malicious sources.
Why Do IP Addresses Get Blacklisted?
IP addresses can be blacklisted for several reasons, including:
- Spamming: Sending unsolicited bulk emails or messages.
- Malware Distribution: Being a source of harmful software intended to damage or disable computers and computer systems.
- Part of a Botnet: Being involved in a network of private computers infected with malicious software and controlled as a group without the owners’ knowledge.
- Phishing Attacks: Attempting to obtain sensitive information such as usernames, passwords, and credit card details by disguising as a trustworthy entity in an electronic communication.
- Suspicious Activity: Engaging in activities that are marked as unusual or potentially harmful based on certain security protocols.
Additional Information Obtainable About an IP Address
- VPN Detection: It’s possible to detect if an IP address is associated with a Virtual Private Network (VPN). VPNs are often used to mask a user’s real IP address for privacy reasons, but they can also be employed for malicious purposes.
- Location: IP addresses can be geolocated to determine the geographical location of the device. This information can be useful in identifying if communications are coming from regions known for high levels of cybercrime.
- Connection Type: Whether the IP is from a residential, public, or corporate network.
- Risk Assessment: Some services provide a risk score based on the IP’s history and behavior patterns.
Why You Should Use an IP Insights for Fighting Fraud
- Block Bad Actors: Known bad actors can be instantaneously identified and blocked by seeing that their IP address has previously been used for fraudulent activity.
- Identify Red Flags: Rules can be setup to identify unusual or suspicious attributes, such as the location of an IP address, whether it’s on a VPN, if it’s from a corporate or private network, and much more.
- Prevent Spam: Blacklists help in filtering out unwanted spam, which can often be a carrier for malware.
- Enhance Security: By blocking IPs known for malicious activities, you significantly reduce the risk of cyber attacks.
- Save Resources: It helps in saving bandwidth and system resources that would otherwise be used to process traffic from these blacklisted IPs.
- Protect Reputation: If you’re running a web service, protecting your users from harmful IPs preserves your reputation and trustworthiness.
- Compliance: For businesses, it helps in complying with data protection and privacy laws by reducing the risk of data breaches.
Understanding and utilizing IP blacklists and insights is a crucial aspect of preventing fraud and maintaining cybersecurity in today’s digital world. By effectively blocking communication from suspicious sources, organizations can significantly reduce their exposure to a wide range of fraud and cyber threats. Additionally, the ability to gather more detailed information about an IP address enhances overall security measures, providing a more robust defense against potential cyber attacks.
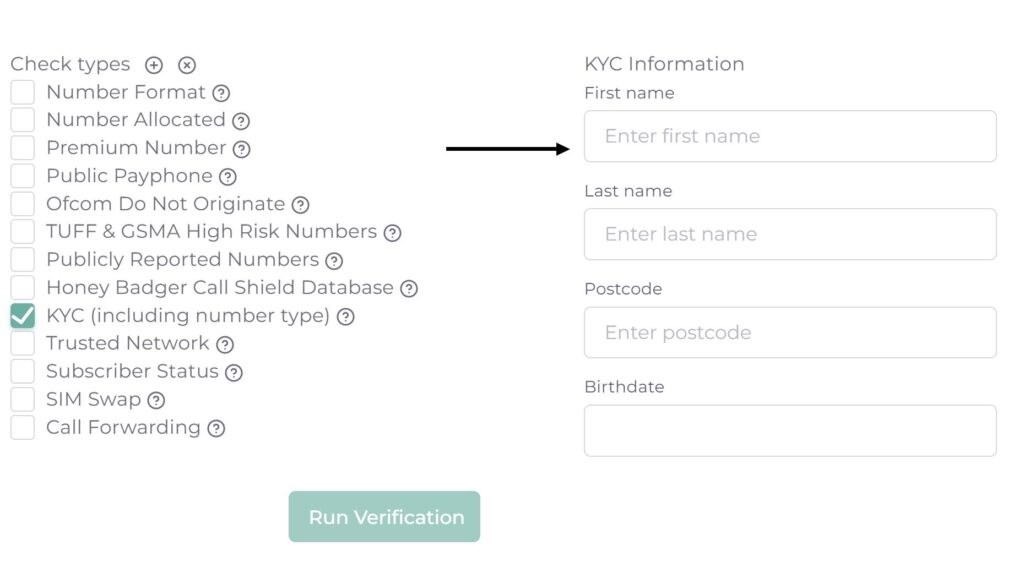
How can Honey Badger help?
Use Honey Badger to instantly lookup an IP address via API or through our Risk Insights web portal. Each lookup provides a risk score along with a breakdown of all the information gathered on an IP address. To find out more visit Honey Badger’s Risk Insights page.