Silent
Authentication
Passwordless Authentication | Powered by Mobile Networks
Created in partnership
Silent
Authentication
Passwordless Authentication | Powered by Mobile Networks
Created in partnership
> Introducing Silent Authentication+
Passwordless, Frictionless & Secure
Authenticate users silently by leveraging the same system mobile networks use to secure phone calls and data sessions.
Authentication Requested
Honey Badger prompts the mobile network to send a random number to the user’s SIM.
Token Generation
Both the user’s device and the mobile network use a cryptographic hash to generate a token.
Token Comparison
Honey Badger coordinates with the user’s device and the mobile network to compare the tokens.
Authentication Result
If the tokens match then the user is in possession of their two factor device and is authenticated.
> Frictionless Authentication
Remove authentication as a barrier
Create seamless authentication experiences like this
But don’t stop there.
Use Silent Authentication+ for
> The plus in Silent Authentication
In-built fraud prevention by design
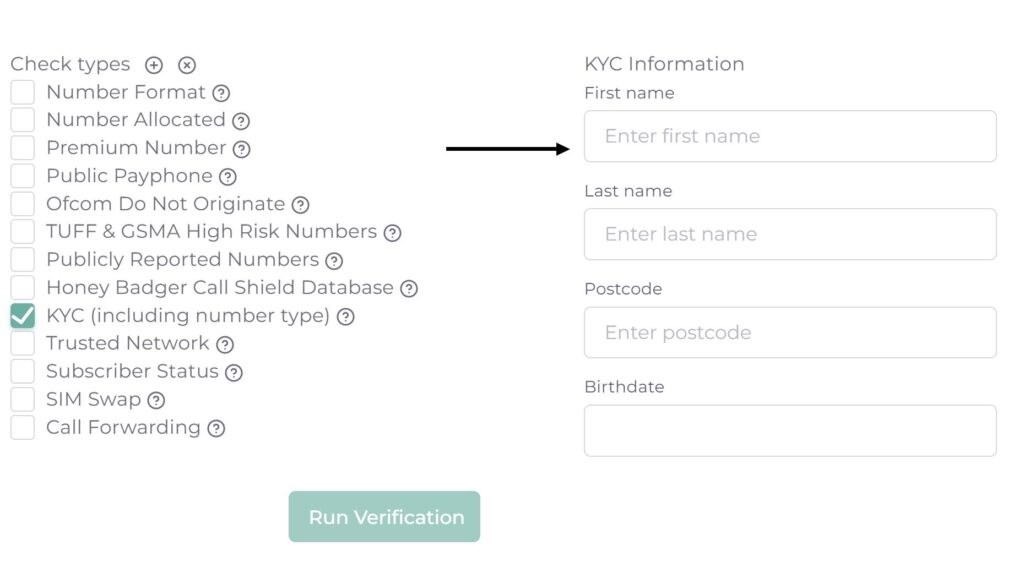
We’ve put the plus in Silent Authentication by incorporating additional fraud prevention checks. When setting up Silent Authentication simply select the fraud checks you’d like to include before user authentication begins. If a fraud check fails then authentication will be paused, protecting you from bad actors.
Check a mobile number for recent SIM swaps, a common attack vector used to facilitate account takeover.
Perform identity verification by comparing firstname, lastname, postcode or date of birth with the data held on file by mobile network operators.
Check if a mobile device is currently overseas, an indicator that the person your dealing with is masquerading as a local.
Check if a mobile number is forwarding all traffic on to a different number, a common tactic used by fraudsters.
Check if a mobile number is a high rate premium number, a common tactic used by fraudsters to generate revenue.
Check if a mobile number has been reported by members of the public for malicious or suspicious activity.
Check if a mobile number is on Honey Badger’s database of fraudulent numbers, reported by over 35 consortium members.
Check if a mobile number is on Ofcom’s Do Not Originate list, which contains blocked and reserved numbers.
> Getting Started
Out with the old, in with the new, we’ve got Silent Authentication+ libraries just for you
Using Silent Authentication+ in your apps and services is easy with our purpose built libraries. You can authenticate users with a single API call, take care of handover from desktop to mobile, and configure any additional fraud checks.
> Contact
Speak with a Silent Authentication+ expert
Honey Badger helps companies operate by reducing and mitigating risk. Speak with an expert to discover how Silent Authentication+ can work for you.
Drop us a message and we’ll be in touch right away.
> Resources
Find more resources on Silent Authentication+ and other Honey Badger solutions


















Complete the form below and we’ll be in touch to arrange access to the Honey Badger API and documentation.
Stop fraud and improve customer experience during account servicing by eliminating SMS One Time Passwords (OTP). Instead, leverage phone based SIM authentication which involves comparing data generated by the Mobile Network Operator (MNO) with mobile device session data. This provides a foolproof way of proving that an individual is in possession of their two-factor device.
This new approach to authentication isn’t susceptible to SIM swap attacks and doesn’t require the user to enter a password. Ultimately, account takeover attacks are blocked, while customer experience is improved and the time taken to service a request us reduced.

Contact Data Cleansing verifies that the contact and personal information you hold isn’t out of date or inaccurate. Data is compared against the information held on file by Mobile Network Operators (MNOs). Whether processing a single record or sanitising thousands of records in batch, you’ll quickly identify bad data.
The case for maintaining up-to-date records goes way beyond good practice for compliance and regulatory reasons. It’s critical to ensuring customers are contactable. Furthermore, it reduces security threats by ensuring communications aren’t sent to the incorrect individuals.

SIM Swap Detection is a critical step in stopping account takeover. Why? Because account takeover attacks commonly exploit the ease of which a phone number can be stolen by simply assigning it to a new SIM. This allows bad actors to intercept communications, such as SMS one-time-passwords (OTP), which are used by 93% of enterprises worldwide to verify customers.
SIM Swap Detection instantly and silently checks the history of a SIM card to see when it was last swapped. Recent swaps indicate high risk of fraud, allowing you to take appropriate action, such as failing verification or requesting additional security procedures are followed.

Social Trace significantly reduces the risk of losing contact with your customers by diversifying communication channels. Simply drop the Social Trace widget into your onboarding workflow and allow customers to connect one or more social channels with just a click.
Lenders who capture social channels are significantly less likely to lose contact with their customers. Why? Because different demographics prefer to engage over different channels. This is particularly important when it comes to collections. Initiating contact over different channels increases your chances of getting a response, which in turn increases the likelihood of resolving late or non payment.

Mobile Fraud Check allow you detect fraud indicators using data provided by Mobile Network Operators (MNOs). Key checks include device overseas, call forwarding, SIM swap, a high risk number database lookup and much more.
Furthermore, Mobile Fraud KYC allows you to verify a person’s firstname, lastname, date of birth and postcode against the data held on file by MNOs. Since MNOs conduct their own KYC checks on new customers, it gives you the ability to match personal information you collect against a trusted and verified source.
Mobile Fraud Checks happen instantly and with zero customer friction. The data held by MNOs is often more recent and reliable than other data sources and a level of granularity is provided, allowing you to see how many and which KYC fields matched.
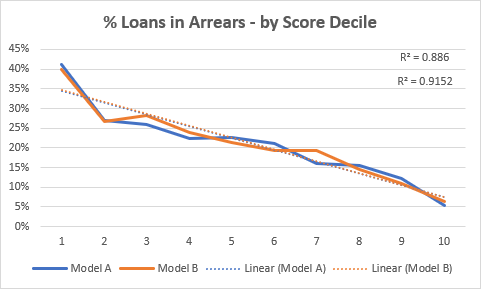
Mobile Data for Credit Risk delivers the data required to predict credit risk based on a persons mobile phone information. Key data attributes include the network provider, line type, and KYC match information. Working in partnership with lenders we’ve been able to clearly identify correlations between this data and the likelihood of a loan going into arrears.
Open Banking Vs Mobile Data. Which is the most effective in predicting bad borrowers? A recent project with a UK lender compared a risk model built with Open Banking against a model built with Honey Badger’s Mobile Data. The results showed that both models outputted almost identical risk scores. The difference? Mobile Data could be deployed immediately with no customer friction required to calculate a risk score.
PAY PER LOOKUP
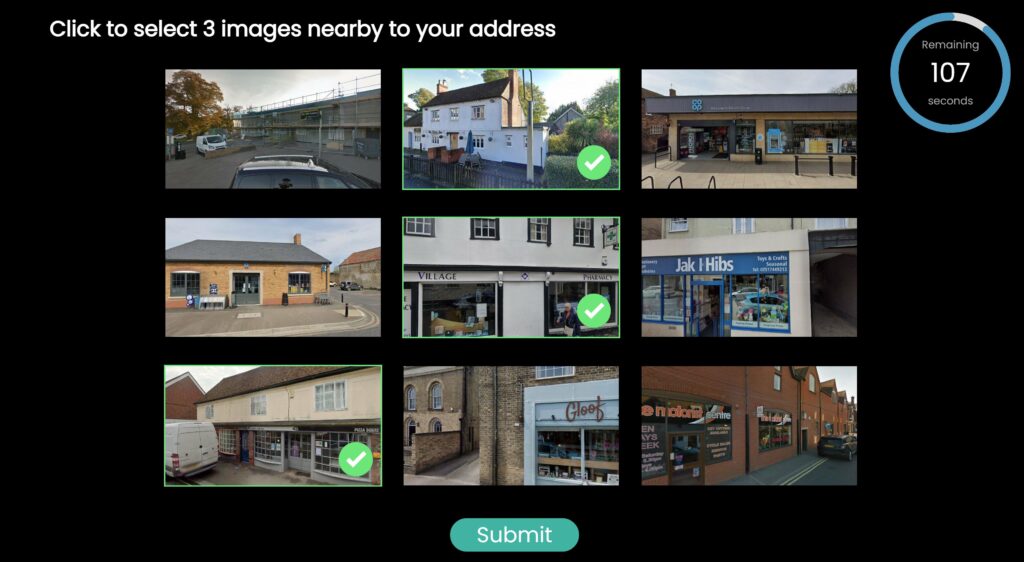
Geo Authentication™ provides frictionless identity verification that reduces abandonment rates. Users simply select images that they recognise from nearby to their address. In built anti-fraud controls ensure that valid users can complete the challenge whilst bad actors are blocked.
Leading lenders such as Amplifi Capital use Geo Authentication during applications as an alternative to more intrusive identity verification checks, such as document uploads, that cause high friction and lead to increased dropouts. Completion rates with Geo Authentication are 28% higher and have subsequently helped drive an increase in revenue for the business.