SMS One-Time Password (OTP) is the most widely used two-factor authentication (2FA) method, and it’s not hard to see why: SMS OTP works universally without the need for clunky authenticator apps, doesn’t require specialist hardware like biometric solutions, and maintains backwards compatibility as devices and operating systems evolve over time.
Why then, are we so excited by a new 2FA solution we’ve named Silent Authentication? Is it love or lust? Let’s dig deeper and find out…
To appreciate Silent Authentication you must first understand the pitfalls of SMS OTP. The biggest flaw being that they are no longer considered secure. Bad actors have for a long time exploited SIM swap attacks which involves tricking phone company employees into porting a customer’s phone number to a new device and SIM card, resulting in SMS OTPs being sent directly to the bad actors.
In recent years fraudsters and scammers have become even more deceptive by using social engineering techniques to intercept SMS OTPs sent directly to users. This is commonly known as a man-in-the-middle attack and is often facilitated by a bad actor contacting the user under the pretence of being an employee at a trusted organisation. Subsequently, they ask the user to read out the SMS OTP they’ve just received for security purposes, thus intercepting the code and allowing them to take control of the user’s account.

If the security vulnerabilities of SMS OTP don’t faze you (and they should!) then also consider the customer friction they present. It can take up to 40 seconds to receive, enter and validate an SMS OTP. Customer friction is particularly high when accessing services from desktop or laptop devices, which require handover to a mobile device with SMS functionality, followed by the user manually typing in the code they’ve just received. The same laborious and frustrating handover process can be said for authenticator apps. If 40 seconds doesn’t seem like long, then consider that just one login to a service daily using this approach equates to just over 4 hours spent logging in over the course of a year!
Introducing Silent Authentication
With the limitations of SMS OTP in mind let’s explore Silent Authentication. Unlike SMS OTP and other passcode based solutions, Silent Authentication eliminates the need for a code altogether (gasp!). Instead, it uses the mobile network to determine that a user is in possession of a phone number. That might sound a little cryptic, but don’t worry, it’s simpler than it sounds.
At a high level, rather than sending an OTP, a one-way function is used to generate a token on a user’s device without requiring any interaction from them. At the same time, the Mobile Network Operator is instructed to contact the SIM to which the phone number is registered and generate a token of its own (using the same one-way function). Finally the two tokens are compared. Et voilà! If the tokens match then the user is in possession of the device and they are authenticated.
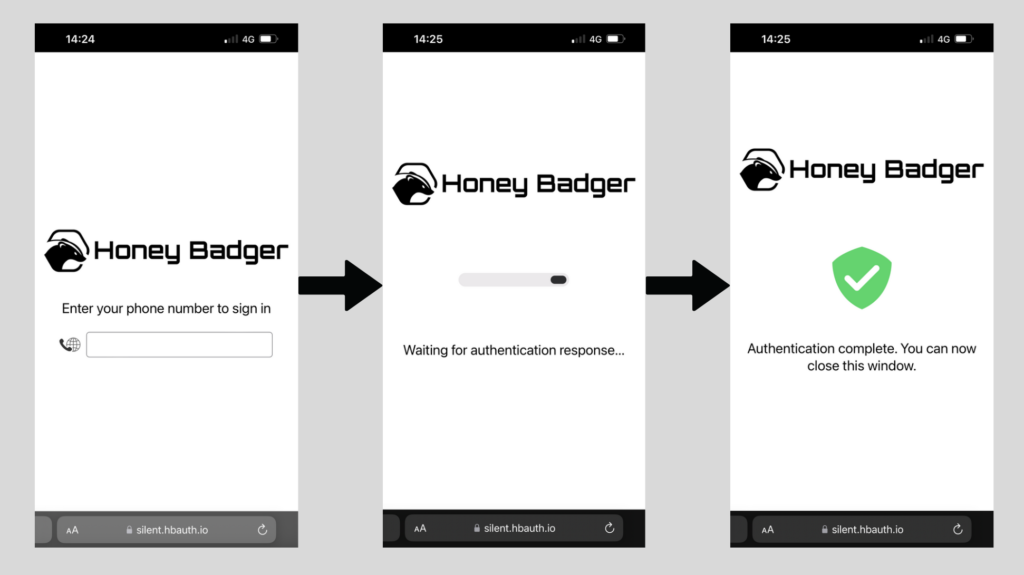
The result is a streamlined two-factor authentication process that takes 3 seconds on average. Authentication can be triggered by entering an identifier (such as phone number as shown above), or simply by the press of a button.
What about other benefits?
You guessed it, Silent Authentication isn’t just about reducing friction and creating better customer experiences. Here are 6 other benefits of Honey Badger’s Silent Authentication solution that you should be aware of:

Not susceptible to social engineering and phishing
Since there’s no passcodes involved there’s nothing for fraudsters to intercept.

Silent Authentication is built on top of the Global System for Mobile Communications (GSM) standard that mobile network operators use to authenticate phone calls and data sessions.

Reduced support costs
With less friction and reduced reliance on users to remember passwords, wait for OTPs, download authenticator apps or enter codes, comes significantly less load on customer support teams.

Increased coverage and device compatibility
Silent Authentication isn’t limited by devices types and OS versions like biometric solutions.

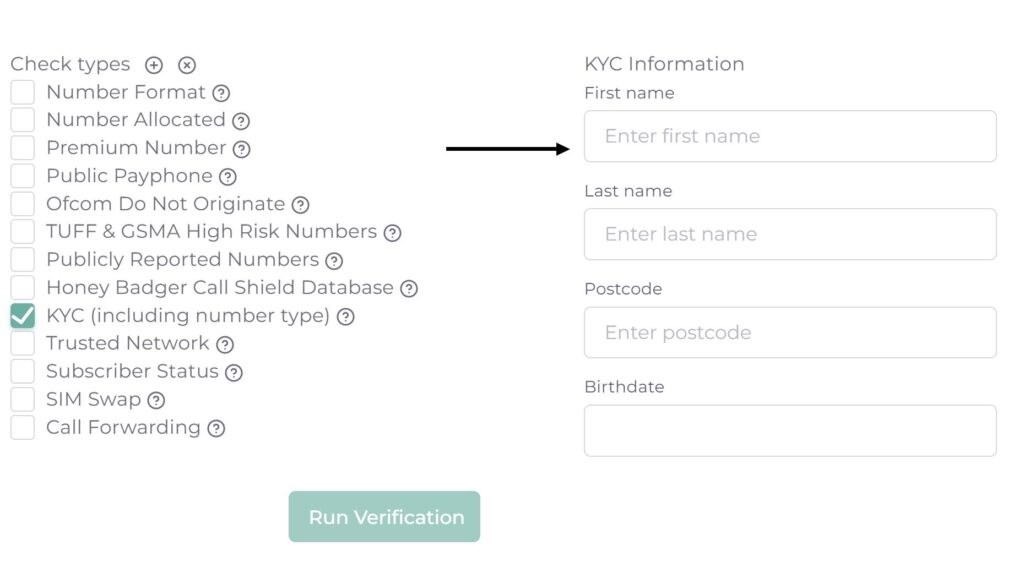
In-built SIM swap checks and automatic failover to SMS OTP
Honey Badger’s Silent Authentication solution incorporates SIM swap checks, with automatic failover to SMS OTP when mobile network based authentication isn’t available ensuring users can always authenticate securely.

Honey Badger can automatically detect non mobile devices and generate QR codes that users simply have to scan with their mobile device to complete authentication.

Silent Authentication. So is it love or lust?
With the drive towards passwordless and the limitations posed by SMS OTP we’re 100% in 
Get a demo of Silent Authentication
Enter your email address and we’ll send over some times for a demo.
Honey Badger HQ