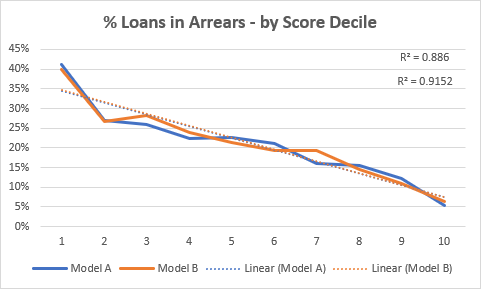
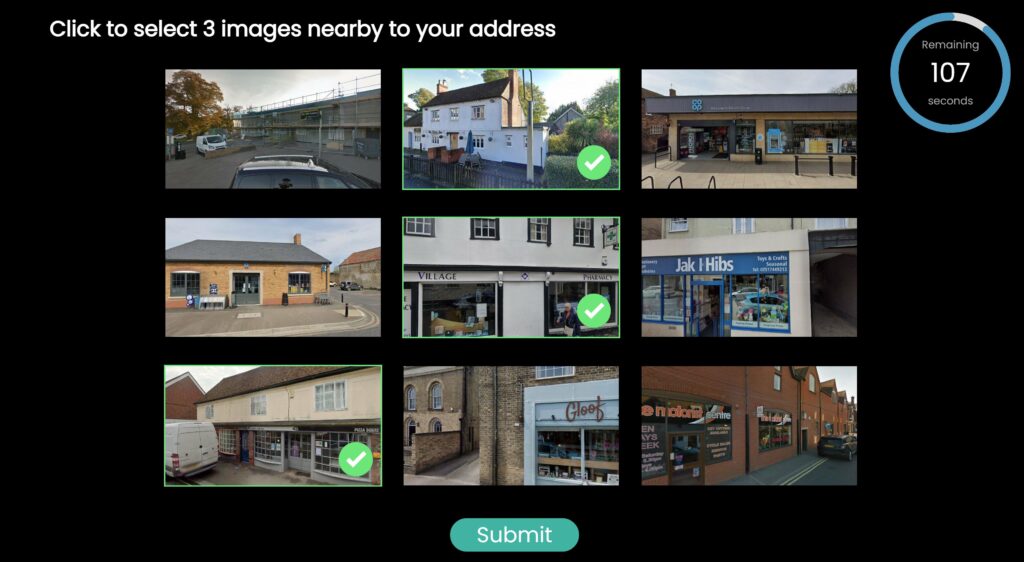
As you tap your smartphone to make a call, send a text, or access the internet, have you ever wondered how the network verifies if you are who you claim to be?
OK we get it, unless you’re a cyber security geek, you probably haven’t wondered too much about it.
But since it’s now possible to leverage the same system mobile networks use to authenticate users, a passwordless world just got a lot more feasible. And because Honey Badger is at the forefront, allow us to uncover the fascinating world of mobile network authentication.
The Importance of the SIM Card
The heart of mobile authentication starts with the humble SIM card. But this tiny chip is more powerful than most realize:
International Mobile Subscriber Identity (IMSI): Think of the IMSI as the unique ID card for your phone. It’s primarily used to identify you as a subscriber but isn’t directly employed for security to avoid potential misuse.
The Secret Keeper, Authentication Key (Ki): Embedded within the SIM is a secret key, aptly named Ki. It’s a cryptographic secret that’s shared with your mobile operator’s Authentication Center (AuC). Crucially, the Ki never openly travels through the airwaves, ensuring its confidentiality.
Engaging in a Secure Dance: Challenge and Response
When you power up your phone and it seeks to connect to the network, a digital “handshake” unfolds:
The network, like a guard at the gates, issues a challenge by sending a random number to your device.
Your device processes this number with its Ki to produce a response, which it sends back.
In parallel, the AuC, using its copy of the Ki, computes an expected response.
If the two responses match, the gates open! Your device is authenticated.

OK OK, we know it sounds technical. But think of it this way, the mobile network has proven it’s you by using your SIM and device to generate a token. If you weren’t in possession of your SIM, then the token generated wouldn’t match with what the mobile network expects, and you wouldn’t be authenticated. It’s similar to when an SMS OTP is used to prove you’re in possession of a device, except it’s more secure and there’s no need to enter an OTP code.
The Best Part: You can Leverage this Process!
For the most part mobile network authentication is a closed ecosystem, reserved only for carriers to secure calls, texts and data sessions. Until now that is. Mobile Network Operators across the globe have begun allowing other apps and services to piggyback off their uniquely secure authentication mechanism.
The result? A way to prove a user is in possession of a device without clunky SMS OTP’s or magic links. It’s so seamless in fact that we’ve named this new approach Silent Authentication+. But maybe best of all, it dramatically reduces the risk of fraud through man in the middle and social engineering attacks. For more benefits be sure to read our blog post on why we’ve fallen in love with Silent Authentication+.
How does Honey Badger fit in?
You might be forgiven for wondering where Honey Badger fits into the brave new world of Mobile Network Authentication. The answer is that we’ve removed the barriers to getting started by building Silent Authentication+ libraries and software development kits (SDKs) native to web, iOS and Android.
Get started with our Silent Authentication+ libraries, which make authentication via the mobile network a breeze!
We’ve removed the technicalities of underlying protocols and taken care of the commercial relationships with mobile network operators. Ultimately, giving you the ability to authenticate users via the mobile network in just a couple of seconds using a single API call. Nice!
Hungry to learn more? Schedule a call with one of our experts or request a demo using the form below 
Get a demo of Silent Authentication+
Enter your email address and we’ll send over some times for a demo.
Honey Badger HQ